How to Secure Your API Against Attacks and Intentional Misuse
Hiring a New York or Menlo Park white-shoe law firm to write your app’s Terms of Service (ToS) might bring peace of mind, but how do you ensure that your expensive rules are actually adhered to. Just like the pervasive abuse of customer review guidelines in B2C companies, B2B companies also suffer from multiple/unverified review problems.
Similarly, by their design, APIs are also vulnerable to misuse by bad actors, but this time through brute force attacks. How do you secure your API platform against both types of abusive practices?
Use Cases
Online reviews should have been a panacea for impartial and helpful perspectives on products and services. Unfortunately, all too often, reviews of restaurants on Yelp or products on Amazon are hijacked by nefarious forces. For example, Amazon deleted 20,000 suspicious reviews following a Financial Times investigation, whilst in 2019 Yelp issued more than 1,300 alerts about businesses brazenly attempting to manipulate ratings and reviews.
To maintain user trust, it’s important to uphold the integrity and quality of the content on your platform. If certain users flout your ToS and abuse your API to create multiple reviews, then the credibility of your solution will suffer and your customers might go elsewhere. It’s important to catch those that are spamming your service as early as possible.
APIs provide an easy to use, flexible and scalable interface for developers. Unfortunately, that’s also the feature set preferred by the attacker community. By restricting API access to those who have authenticated their accounts with you, a decent level of protection is ensured.
However, if a bad actor decides to probe your platform by using a brute force attack, then your accounts could become compromised. If that happens, negative user trust and brand equity, not to mention legal repercussions, could ensue. Therefore, it’s super important to detect such attacks and warn the affected customers, before their account is blocked and they’re locked out of API access.
Playbook for Securing Your API Against Intentional Misuse and Attack
Automating repetitive processes is a key attribute in whole-product design. By combining advanced User Behavior Analytics (UBA) with behavioral emails, Moesif’s able to make you more productive through sophisticated workflows of many functional, performance and product issues.
This demonstration playbook focuses on protecting against ToS violations and attacks, specifically illustrating Moesif’s capabilities by showing you how to deal with warning users who created too many reviews or alerting users with too many unauthorized errors in last 7 days.
Other playbooks focus on Automating Notification of Quota and Billing Issues and How to Guide Customers on API Integration Automatically with Moesif. The three playbooks only really scratch the surface of what’s possible with our platform; Once you get the hang of creating your own cohorts, specifying triggering events and designing behavioral emails, you’ll wonder what you ever did before Moesif.
List of Ingredients
We’ll be using Moesif’s analytics tool to build this app. If you haven’t yet created an account you can sign up for free.

Steps in Playbook Creation
Playbooks include workflows, SOPs, and cultural values, that go together to shape a consistent response — the play. Irrespective of what you’re trying to achieve, Moesif playbooks contain two key elements: cohort specification and email creation.
Cohort Specification
Moesif defines user and company as distinct entities, ones which can be grouped into cohorts sharing similar criteria. Distinct cohorts include those sharing similar fields, such as: subscription plans, endpoint usage, request codes, etc. Cohorts can be created by filtering on user/company demographics and actions, as explained in an earlier tutorial.
To create a new user cohort go to the Users > User Lookup section of the Moesif tool and simply choose fields from the pulldown menus Users that match and Performed events, as shown below. The full list of event filters and user/company fields can be found in our user-analytics pane.
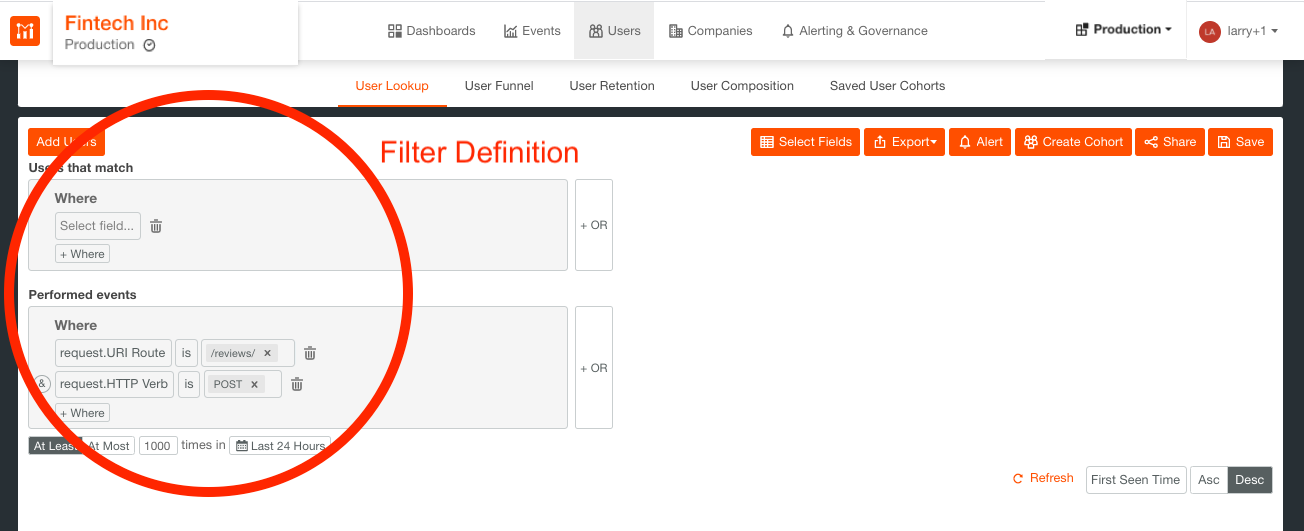
Warning users who create too many reviews
To create a cohort of those misbehaving users select from Performed events the filters: request.URI route is /reviews/ and request.HTTP Verb is POST, and then set the time period as At Least 1000 times in Last 24 Hours, as shown below.
Alerting users with greater than 100 unauthorized errors in last 7 days
To create a cohort of users with > 100 unauthorized errors in last 7 days go to Users > Saved User Cohorts and in Performed events select the filters: response.Status.Code is 403 Forbidden (0) and then set the time period to At Least 100 times in Last 7 Days, as shown below.
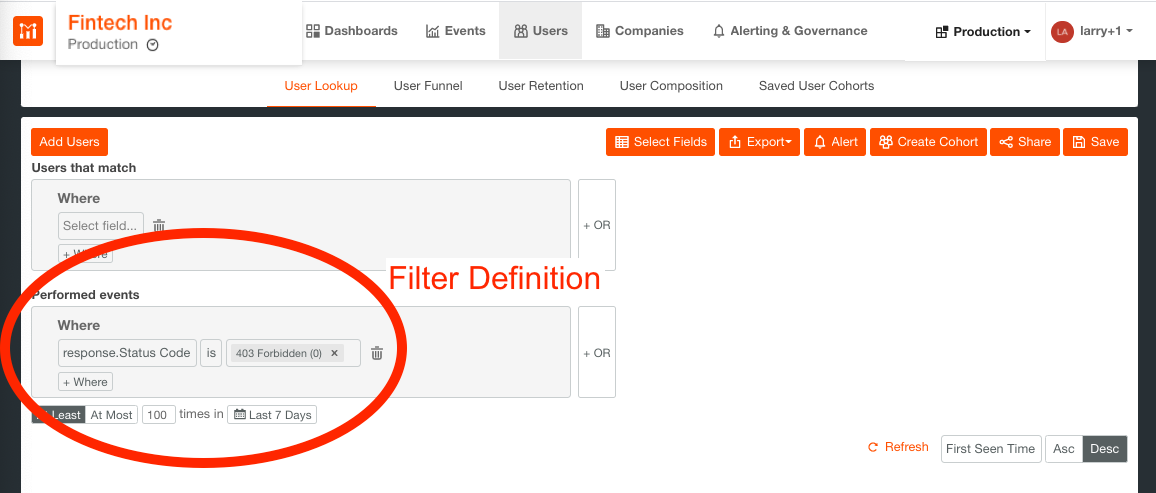
Once filters are set, Moesif will look through all current and historical data and group together all of the users/companies that fulfill the filters’ criteria. We’ll also monitor whether the users/companies continue to belong to that cohort, without any manual intervention.
The cohort can then be used to populate the recipient list in a behavioral email.
Behavioral Email Creation
You can design HTML emails right in Moesif using a drag-and-drop WYSIWYG editor. To create a behavioral email go to the Alerting and Governance > Behavioral Emails section of the Moesif tool.
The first step is to add a new +Template, where the template includes both the email design as well as other pertinent info, such as which cohorts should receive the email. Full documentation on creating email templates is available, but suffice it to say, email creation is pretty straightforward and, once complete, emails can be verified using the Test button.
Warning users who create too many reviews
Simply add the pre-defined cohort to the recipient’s list of the behavioral email notifying them that they’ve created too many reviews and violated your ToS:
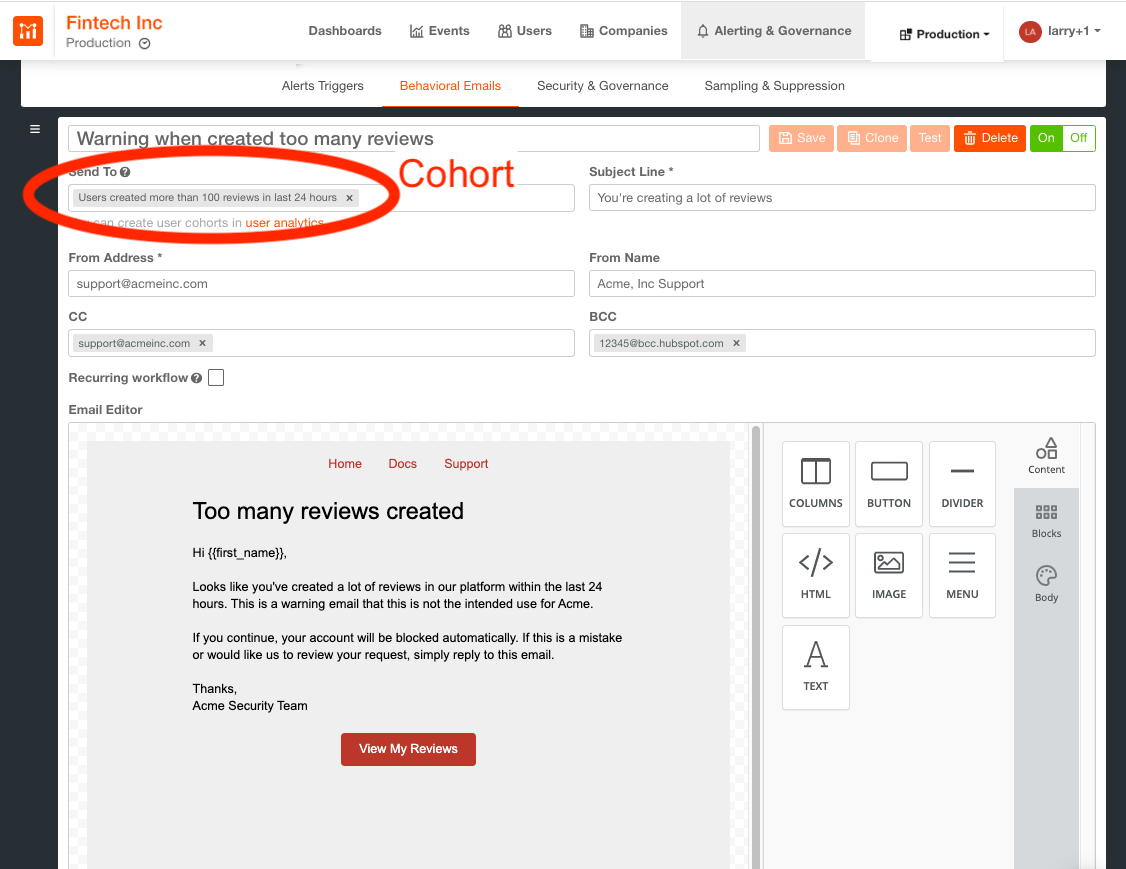
Whenever new customers exceed 1,000 reviews in the last 24 hours they’ll automatically be added to the cohort, and an email will be sent.
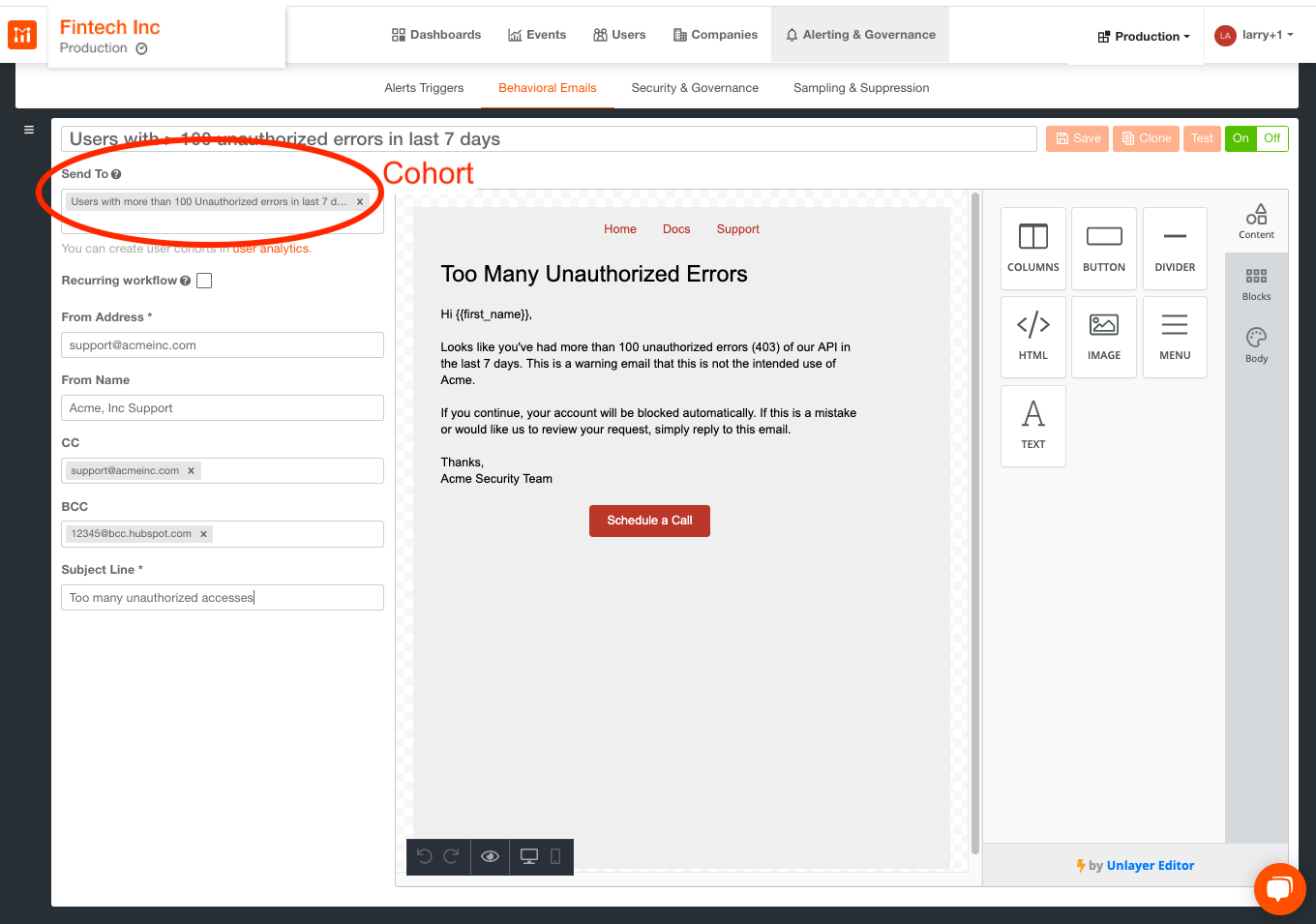
Alerting users with greater than 100 unauthorized errors in last 7 days
Similarly, simply add the cohort of users you’ve previously defined to a behavioral email which will then be triggered whenever multiple unauthorized accesses occur:
Takeaways
Maintaining user trust and brand equity has never been more important. Identifying and notifying those who violate your ToS, or giving your customers a heads up that their account might be the subject of a brute force attack, are all part of good product governance.
With our SaaS platform, we strive to make our customers as productive as possible. Through the combination of payload observability and behavioral emails, we’ve created automated warning processes that save you time and resources.
 Save Time And Resources With Behavioral Emails Workflows
14 day free trial. No credit card required.
Learn More
Save Time And Resources With Behavioral Emails Workflows
14 day free trial. No credit card required.
Learn More




